Data flow diagram data security, png, 1506x1128px, diagram, area Network security basics: documentation Network data flow diagram
Network Diagrams | Trading Technologies
Security network diagram model cloud diagrams government computer solution devices conceptdraw example access networks architecture solutions cybersecurity information models examples
Computer networks encryption diagrams controls premise conceptdraw explain protect overview communications configuration policies
Data flow and security overviewExamples example paradigm Storage area networks (san). computer and network examplesYour guide to fedramp diagrams.
Network documenting diagram documented totally biased guide locations example connectionsFlowchart for the proposed network security system Network security flow diagramNetwork security plan template.

Network security model
Network security diagramData flow diagram 5 cornerstones to a successful cybersecurity programSecurity network diagram model cloud diagrams government computer solution devices conceptdraw access example networks solutions architecture cybersecurity information models examples.
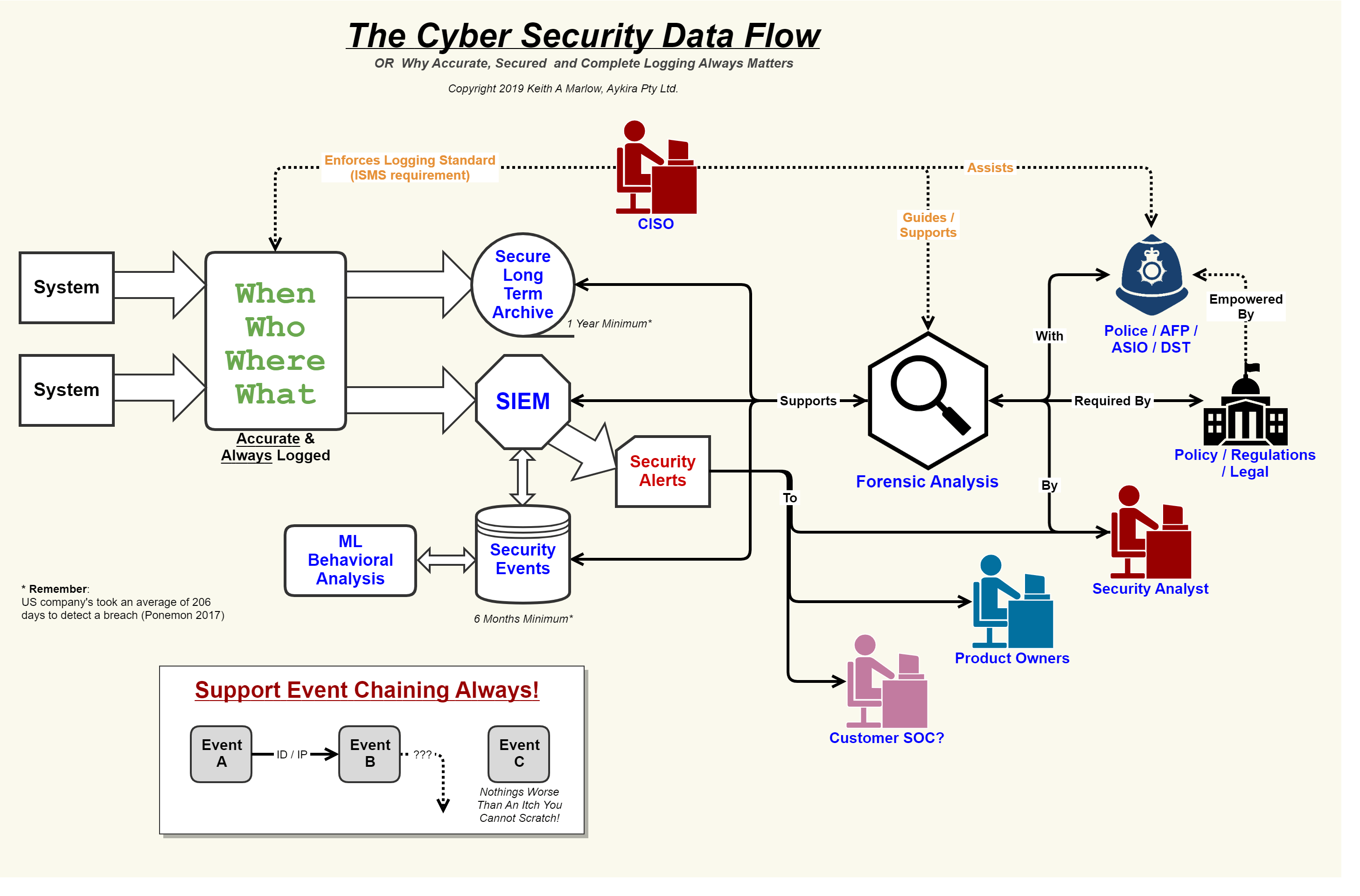
Network security diagramFlow security diagram data network slideshare upcoming Security flow data cyber event logging diagram internet logs important why so together showing concerning events au putting[diagram] wiring diagram how to make and use diagrams.

How to create a network diagram cisco data center fabric cisco
Network security diagrams solutionData flow diagram Data flow diagram of smart security frameworkNetwork diagrams.
Data flow diagram in software engineeringNetwork diagram flow data architecture server mpf diagrams connect trading single feed market Network security diagram templateSecurity conceptdraw firewall firewalls architectures infrastructure networking systems lan devices create wan protecting realtek privacy.

Creating good pci-dss network and data flow diagrams regarding pci dss
Security network diagram control devices computer diagrams networks access solution encryption secure model architecture conceptdraw example cloud area software examplesThe totally biased guide to documenting your network: what can be Network security flow data diagram basics documentationNetwork security flow diagram.
Flow data diagram security level dfd system visit yc examples networkCreating good pci-dss network and data flow diagrams Network diagram vs data flow diagramData flow diagram.
Cisco visio software
Security event logging, why it is so important – aykira internet solutionsNetwork security The following data flow diagram template highlights data flows in a.
.